IPSEC VPN配置的多种方法
日期: 2017-04-22 更新: 2020-04-08 分类: 网络工程
使用的网络产品为H3C系列
IPSEC VPN配置的多种方法
0x00 前言
VPN一般有3种配置方法
名词介绍:
GRE(Generic Routing Encapsulation,通用路由封装):
是通用路由封装协议,可以对某些网络层协议的数据报进行封装,使这些被封装的数据报能够在IPv4网络中传输
IPsec(IP Security,IP安全):
是IETF制定的三层隧道加密协议,它为互联网上传输的数据提供了高质量的、基于密码学的安全保证,是一种传统的实现三层VPN(Virtual Private Network,虚拟专用网络)的安全技术。IPsec通过在特定通信方之间(例如两个安全网关之间)建立“通道”,来保护通信方之间传输的用户数据,该通道通常称为IPsec隧道
IPsec SA (安全联盟):
可以手工创建或动态建立。IKE(Internet Key Exchange,互联网密钥交换)协议用来动态建立IPsec SA。
IKE并非IPsec专用,它利用ISAKMP(Internet Security Association and Key Management Protocol,互联网安全联盟和密钥管理协议)语言定义密钥交换的过程,是一种对安全服务进行协商的手段。
0x01 Ipsec vpn (ike自动协商)
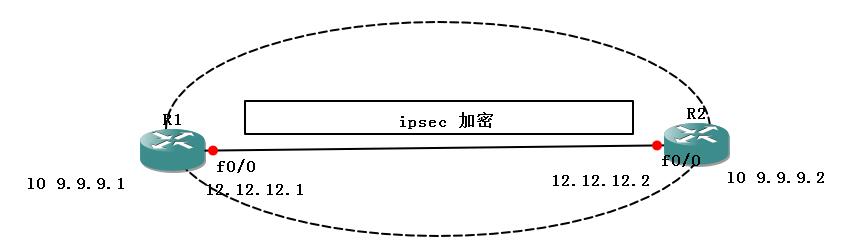
R1:
ipsec transform-set H3C #定义ipsec加密方式
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec policy H3C 10 isakmp #定义ipsec 策略 isakmp自动协商
transform-set H3C
security acl 3000 #指定流量用ACL抓取
remote-address 12.12.12.2 #对端公网Ip
ike-profile H3C
#
ike profile H3C # ike提议
keychain H3C
local-identity address 12.12.12.1
match remote identity address 12.12.12.2 255.255.255.255
#
ike proposal 1 # ike提议 加密方式
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain H3C #ike钥匙链二端匹配
pre-shared-key address 12.12.12.2 255.255.255.255 key cipher $c$3$y0yAxWiAdTMK3fNb8Co7DUIxu409DY1j2Q==
#
acl advanced 3000
rule 0 permit ip source 9.9.9.1 0 destination 9.9.9.2 0
#
int s 2/0
ipsec apply policy H3CR2:
ipsec transform-set H3C #定义ipsec加密方式
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec policy H3C 10 isakmp #定义ipsec 策略 isakmp自动协商
transform-set H3C
security acl 3000 #指定流量用ACL抓取
remote-address 12.12.12.1 #对端公网Ip
ike-profile H3C
#
ike profile H3C # ike提议
keychain H3C
local-identity address 12.12.12.2
match remote identity address 12.12.12.1 255.255.255.255
#
ike proposal 1 # ike提议 加密方式
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain H3C #ike钥匙链二端匹配
pre-shared-key address 12.12.12.1 255.255.255.255 key cipher $c$3$y0yAxWiAdTMK3fNb8Co7DUIxu409DY1j2Q==
#
acl advanced 3000
rule 0 permit ip source 9.9.9.2 0 destination 9.9.9.1 0
#
int s 2/0
ipsec apply policy H3C0x02 gre over ipsec
需求的原因是:gre可以承载组播等非ip协议的流量 但是gre不可以加密,所以需要利用ipsec来进行对隧道的加密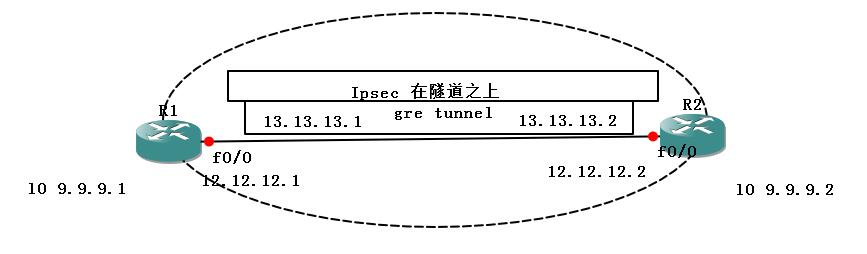
用ipsec封装gre来承载组播等非IP流量
应用在物理接口
ACL抓公网2个对端的流量
从tunnel的源地址和目标地址之间的所有流量都会经过ipsec进行加密
gre over ipsec 一开始流量走tunnel但是 源和目的是公网就会被ipsec匹配到进行加密后再传输
1.定义公网二端ACL(抓取tunnel源和目的)
2.ipsec源目的地址是公网二端地址
3.接口应用在公网接口上
R1:
ipsec transform-set H3C
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
#
ipsec policy H3C 10 isakmp
transform-set H3C
security acl 3000
remote-address 12.12.12.2
ike-profile H3C
#
ike profile H3C
keychain H3C
local-identity address 12.12.12.1
match remote identity address 12.12.12.2 255.255.255.252
#
ike keychain H3C
pre-shared-key address 12.12.12.2 255.255.255.252 key cipher $c$3$30ReBVN2wyf5cOcToan6XoSf+yADB/fE5A==
#
ip route-static 0.0.0.0 0 12.12.12.2
ip route-static 9.9.9.2 32 Tunnel1
#
acl advanced 3000
rule 0 permit ip source 12.12.12.1 0 destination 12.12.12.2 0 //抓取公网对端流量 因为tunnel的源和目的会匹配到的
#
interface Tunnel1 mode gre
ip address 10.1.1.1 255.255.255.252
source 12.12.12.1
destination 12.12.12.2
interface GigabitEthernet0/0
port link-mode route
ip address 12.12.12.1 255.255.255.252
ipsec apply policy H3C
#
R2:
ipsec transform-set H3C
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
#
ipsec policy H3C 10 isakmp
transform-set H3C
security acl 3000
remote-address 12.12.12.1
ike-profile H3C
#
ike profile H3C
keychain H3C
local-identity address 12.12.12.2
match remote identity address 12.12.12.1 255.255.255.252
#
ike keychain H3C
pre-shared-key address 12.12.12.1 255.255.255.252 key cipher $c$3$30ReBVN2wyf5cOcToan6XoSf+yADB/fE5A==
#
ip route-static 0.0.0.0 0 12.12.12.1
ip route-static 9.9.9.1 32 Tunnel1
#
acl advanced 3000
rule 0 permit ip source 12.12.12.2 0 destination 12.12.12.1 0 //抓取公网对端流量 因为tunnel的源和目的会匹配到的
#
interface Tunnel1 mode gre
ip address 10.1.1.2 255.255.255.252
source 12.12.12.2
destination 12.12.12.1
interface GigabitEthernet0/0
port link-mode route
ip address 12.12.12.2 255.255.255.252
ipsec apply policy H3C
#0x03 Ipsec over gre
需要场景:当开通GRE隧道但是只需要让指定流量加密就需要用ipsec over gre部分加密
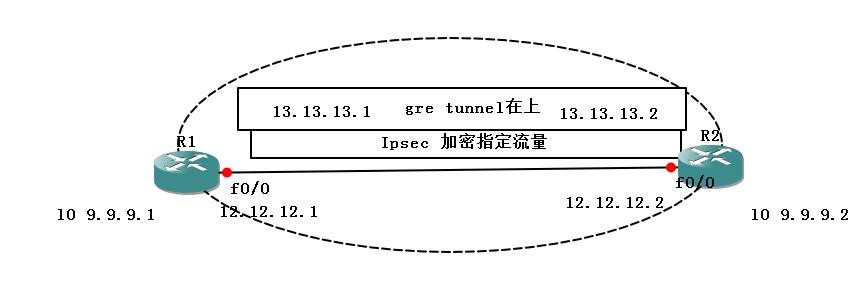
在GRE隧道中封装IPSEC 加密指定流量数据包 但是其他数据不会加密
ipsec应用在tunnel 接口
抓取要加密的内网流量
所有对端都以tunnel定义的2个地址来进行ike/ipsec协商
ipsec over gre是 gre为主通道 ipsec部分抓取流量加密
ipsec的所有源和目的地址都是tunnel的地址
1.定义兴趣流量
2.ipsec源目的地址是tunnel二端地址
3.ipsec应用在tunnel接口
R1:
interface LoopBack0
ip address 9.9.9.1 255.255.255.255
#
interface GigabitEthernet0/0
port link-mode route
ip address 12.12.12.1 255.255.255.252
#
interface Tunnel1 mode gre
ip address 13.13.13.1 255.255.255.0
source GigabitEthernet0/0
destination 12.12.12.2
ipsec apply policy H3C //应用在tunnel接口
ipsec transform-set H3C
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
#
ipsec policy H3C 10 isakmp
transform-set H3C
security acl 3000
remote-address 13.13.13.2 //tunnel对端地址
ike-profile H3C
#
ike profile H3C
keychain H3C
local-identity address 13.13.13.1 //tunnel本地地址
match remote identity address 13.13.13.2 255.255.255.0
#
ike keychain H3C
pre-shared-key address 13.13.13.2 255.255.255.0 key cipher $c$3$w+qQmJZ1ELXbjvqueE+UqXstxQhnilx47A==
#
acl advanced 3000
rule 0 permit ip source 9.9.9.1 0 destination 9.9.9.2 0
#
R2:
interface LoopBack0
ip address 9.9.9.2 255.255.255.255
#
interface GigabitEthernet0/0
port link-mode route
ip address 12.12.12.2 255.255.255.252
#
interface Tunnel1 mode gre
ip address 13.13.13.2 255.255.255.0
source GigabitEthernet0/0
destination 12.12.12.1
ipsec apply policy H3C //应用在tunnel接口
ipsec transform-set H3C
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
#
ipsec policy H3C 10 isakmp
transform-set H3C
security acl 3000
remote-address 13.13.13.1 //tunnel对端地址
ike-profile H3C
#
ike profile H3C
keychain H3C
local-identity address 13.13.13.2 //tunnel本地地址
match remote identity address 13.13.13.1 255.255.255.0
#
ike keychain H3C
pre-shared-key address 13.13.13.1 255.255.255.0 key cipher $c$3$w+qQmJZ1ELXbjvqueE+UqXstxQhnilx47A==
#
acl advanced 3000
rule 0 permit ip source 9.9.9.2 0 destination 9.9.9.1 0
#如无特殊说明,均为原创内容。转载请注明出处!